Enabling MFA in Veeam BR 12
Veeam is now supporting
OTP App MFA in their console application with the release of Veeam Backup and
Replication v12. There is some preliminary work required. It requires a read
through understanding first, but it works.
High
level - While you can only do so much with access to the server,
you can block RDP to it (best practice) and force MFA on local accounts in
Veeam.
The snag is to turn on MFA you cannot use groups, so you
need to add your Administrator or anyone else individually, set Veeam
permissions and remove the default Administrators group.
To skip/block any account from requiring MFA you click on
"this is a service account" and it won’t force MFA.
You then turn on MFA for the system. That enables it for the
user that needs MFA and everyone else that is not a "service
account". It will prompt them with a scannable app code and one you can
cut and paste into an app such as mobile authenticator or ITGlue.
If access to that account is lost, you can reset MFA with
another Veeam admin account. While this might not necessarily stop a malicious
3rd party from trashing the on-premises server. It can help protect from remote access and your
cloud repositories and credentials with another layer.
Here is a deep dive of how to enable Veeam 12 MFA on a Standalone Server:
Step one make sure you have an recent backup of your Veeam Configuration
before you start.
Then Open the Veeam v12 Console and go to Users and Roles.
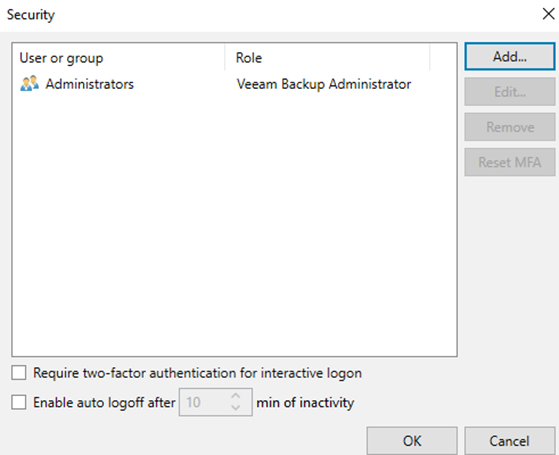
You will notice the Veeam Backup Administrator is
automatically assigned to Veeam Backup Administrators group. From here if you
have not already defined different roles to users you can add them now as well:
Here is list of the Groups:
Here is a link to Veeam Support defining what those group
roles are:
https://helpcenter.veeam.com/docs/backup/vsphere/users_roles.html?ad=in-text-link&ver=120
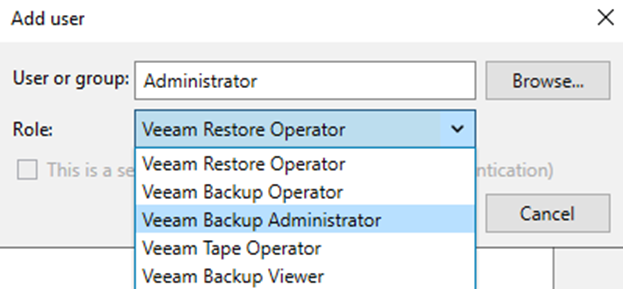
Now we will add a user that is the Veeam Backup Administrator
and once the user is added close Veeam:
Note: you can also set it to log off users due to
inactivity which is another easy step to make sure a malicious user will not take
over an account that was not logged out properly.
When we reopen it we will change the Authentication method and
use the local account and password we already have on the local server:
Notice we have not enabled MFA till we know we have access.
After you add the users exit and log back on as the users individually
to test, before you enable MFA.
Now I am adding a secondary account as a fall back if things
go south with my initial MFA setup. And repeat
the log off and on process.
Now I will delete the BuiltIn\Administrators group.
Caution: If you did not do
the above steps and TEST your access you could lock yourself out soon and be
forced to reload. See Veeam configuration backup note above.
Now I will enable “Require two-facto authentication for
interactive logon” but DO NOT Click OK yet. You need to Edit your users to
setup your non MFA account in case.
For this example we will use Administrator and select “Edit”:
You will see “this is a service account… is no longer grayed
out” so we will select that for this account so it does not require MFA:
For the VeeamAdmin account we will keep it as is:
Note how the Administrator account icon has changed above
I will now log out and log back in as the VeeamAdmin and I
should immediately be prompted to setup MFA using an authenticator app:
Congratulations MFA is now
setup on that account. Repeat as needed for other accounts. Whether you leave a
“service account” without MFA enabled for a back door is your security call but
if you do think through how you will strengthen it without Veeam MFA.
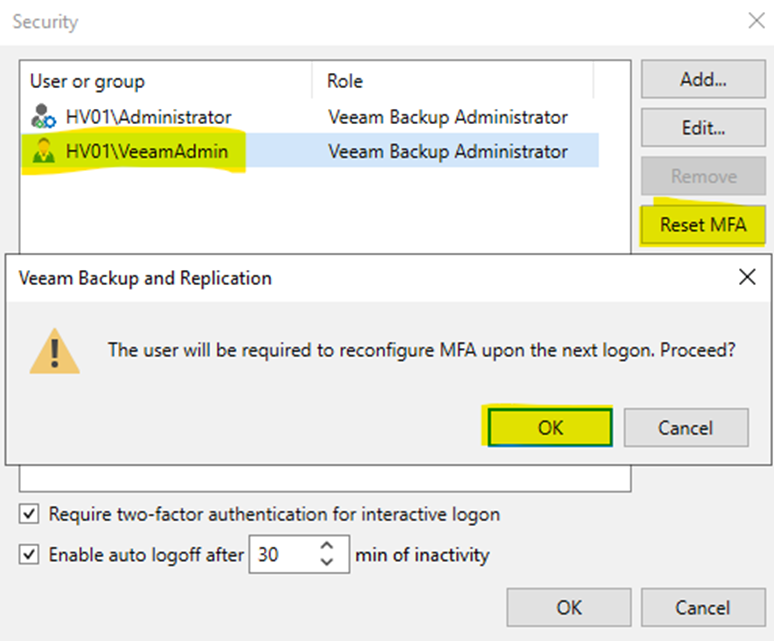
If someones MFA needs reset
you can simply open up the Users and Groups with an active Administrator.
Select the user and "Reset MFA" as shown below:












Comments
Post a Comment